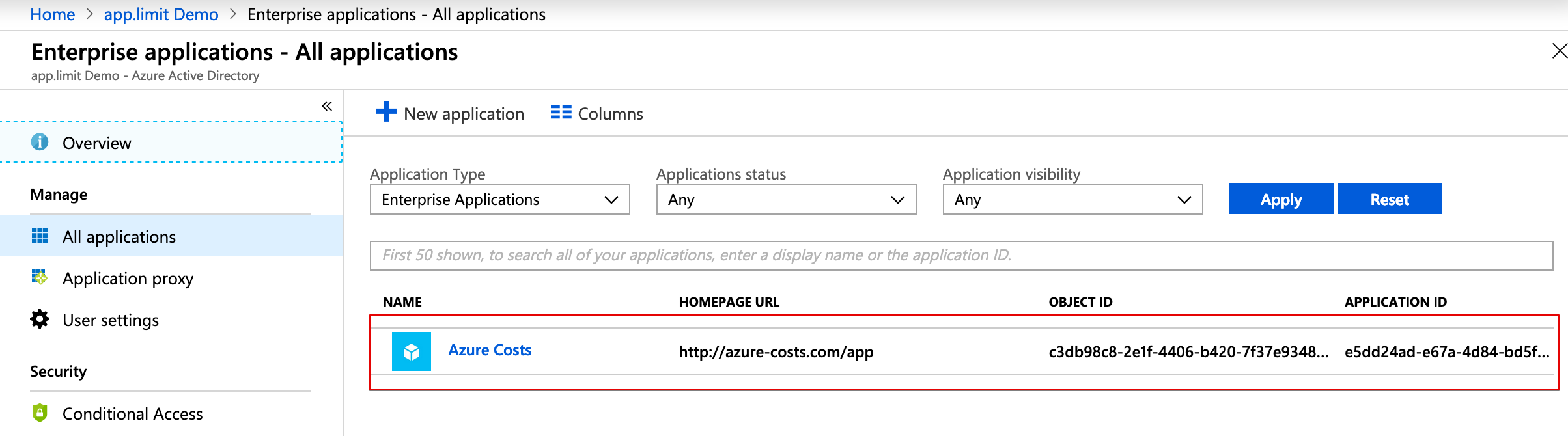
Allow Azure Costs users to login via Azure Active Directory
In Azure Active Directory this settings can be configured for Enterprise Application handling as shown below:
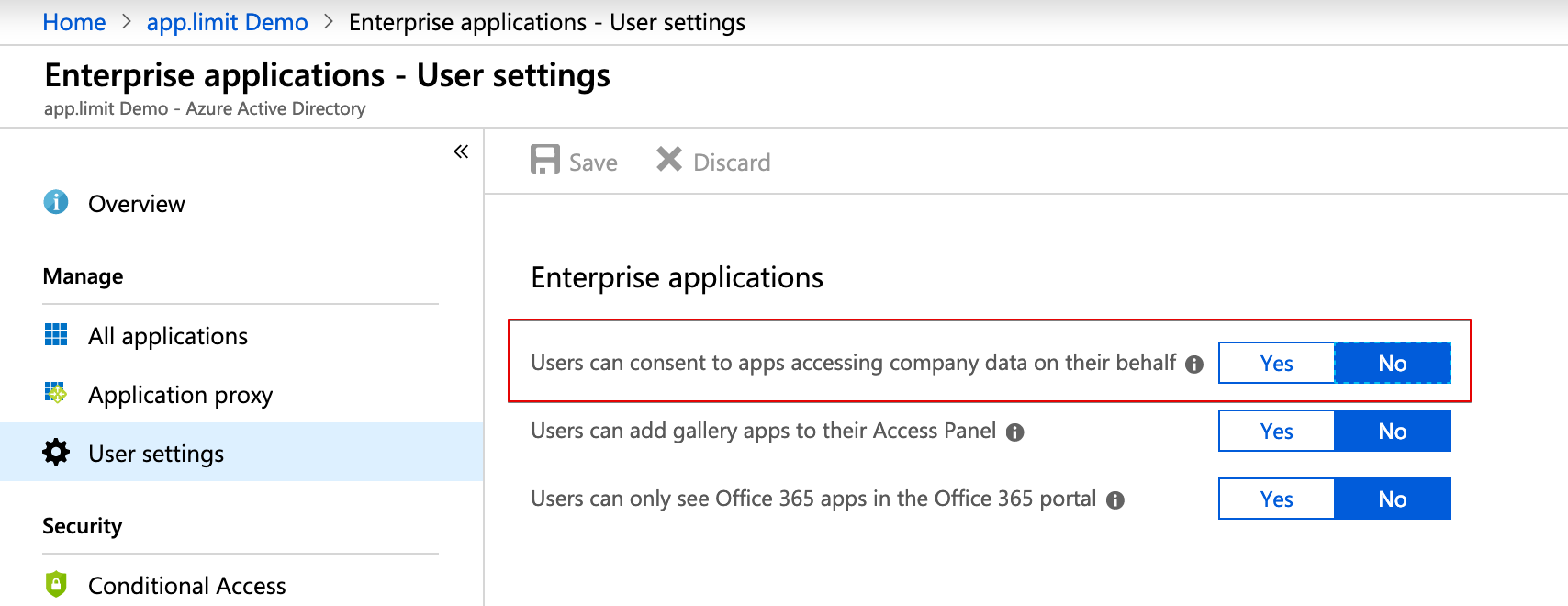
As soon this policy is activated the end user receives the following information during the login on Azure Costs or other 3rd party applications:
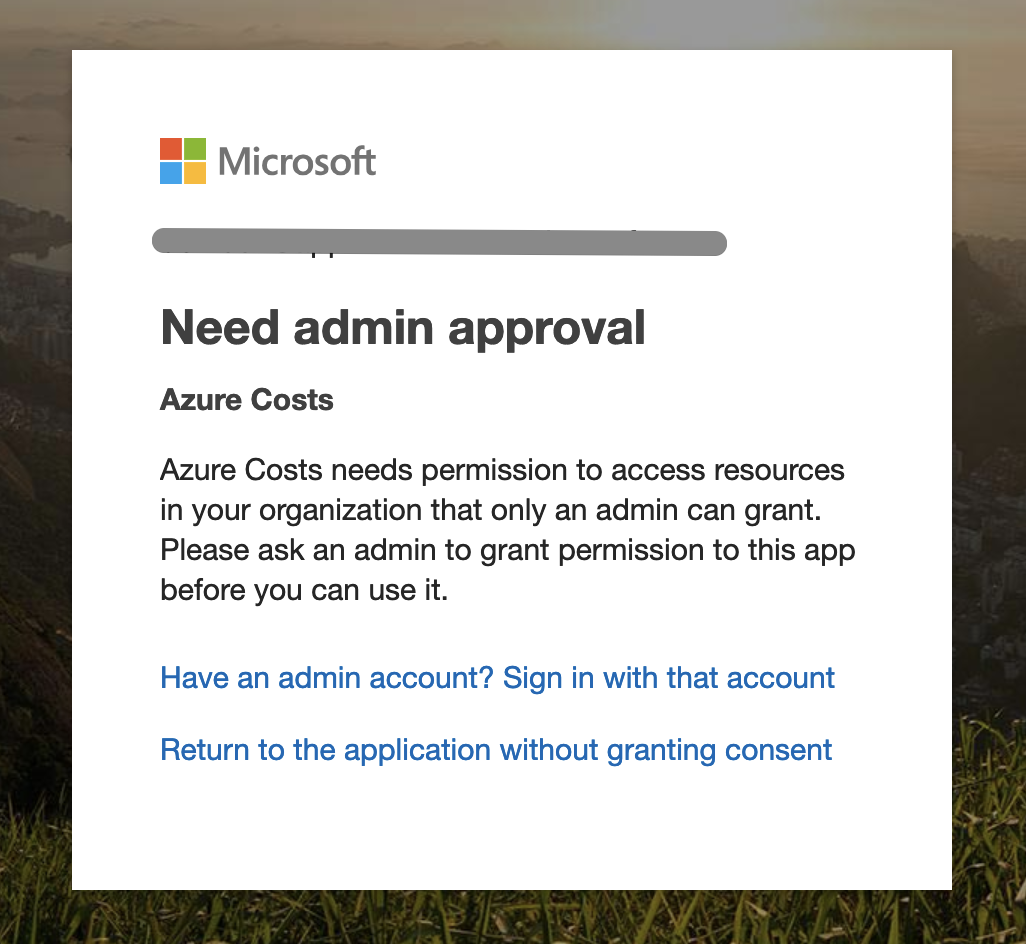
Allowing users consuming Azure Costs with their existing Azure Active Directory account requires a dedicated administrative action, Microsoft calls it Admin Consent Flow. The administrative consent flow is triggerable with the following URL from every Azure Active Directory Administrator:
https://login.microsoftonline.com/common/adminconsent?client_id=e5dd24ad-e67a-4d84-bd5f-7a60587f884f&redirect_uri=https%3A%2F%2Fazure-costs.com
Should more than one Azure Active Directory be managed with the same admin account it's recommended to define the concrete tenant with the following URL scheme:
https://login.microsoftonline.com/{{YOUR AAD Domain}}/adminconsent?client_id=e5dd24ad-e67a-4d84-bd5f-7a60587f884f&redirect_uri=https%3A%2F%2Fazure-costs.com
Customers using the Microsoft Cloud Germany should use the following URL to trigger the Admin Consent Flow:
https://login.microsoftonline.de/common/adminconsent?client_id=489ad96d-b090-4edb-8bcc-b5e05ecb72ed&redirect_uri=https%3A%2F%2Fazure-costs.com
After executing this operation a new application with the name "Azure Costs" appears in the Azure Active Directory and end-user can log into Azure Costs.